2.7.0 changelog (2024-10-08)
- history: always show the integrated address in the destinations table if an outgoing transaction has a payment id
- in some cases, the base address was shown when a payment had been made to an integrated address
- this issue could lead to a potential loss of funds if a repeat payment was made to a service and the address was copied from the dialog without verifying it
- a report of this issue was rewarded with a bug bounty of 2.5 XMR
- on wallets backed by Trezor hardware devices, a warning is shown instead, because the payment id is not stored correctly
- history: you can now import transaction descriptions from a CSV file
- send: improved an error message that is shown when a transaction tries to spend too many inputs
- contacts: paying to a contact now auto-fills the contact name in the transaction description
- coins: ‘send to self’ now sends funds to the change address of the current account instead of the primary account
- settings: added an option to show fiat balance in the statusbar
- nodes: nodes ending with a ‘.local’ tld are now considered local nodes
- nodes: added (more) nodes by plowsof and ofrnxmr to the default list, removed hashvault
- wizard: improved an error message that is shown when the cache file can’t be read
- wizard: fixed an input validation issue on the set lookahead page that could lead to a crash
- revuo: issues now include upcoming events
- macos: fixed an issue that could prevent the application from launching
- flatpak: dates shown in the application should now reflect the system time
- show a notification when a mining payment is received
- fixed an issue that could prevent the application from closing
- fixed a few memory leaks
- updated Qt to 6.7.3
- updated OpenSSL to 3.3.2
2.6.8 changelog (2024-08-15)
- updated Monero to v0.18.3.4
- updated Qt to 6.7.2
- updated Tor to 0.4.8.12
- removed Reddit and LocalMonero plugins
- windows: fixed a graphical issue if windows dark mode was enabled
- trezor: re-enabled bridge transport
- tx pool viewer: fixed table sort
- settings: fixed a potential crash
- wizard: don’t allow illegal chars in file name
- linux: minimum glibc is now 2.31
- update your machine to Debian 11, Ubuntu 20.04 or later
Incident report: Denial-of-Service (28 April 2024) (2024-05-01)
Summary
Feather versions 2.6.5 and below are no longer able to send transactions. Upgrade Feather to 2.6.6 or above to fix the issue.
Users trying to construct a transaction on 2.6.5 and below are presented with the following error message: “Internal error: Unrealistic number of outputs in output distribution”.

The bug was triggered when the number of RingCT outputs on the blockchain exceeded 100 million. This caused a sanity check to fail during transaction construction, resulting in the error shown above.
For approximately 5 hours on April 28, 2024, all available versions were affected by the bug, effectively preventing anyone from transferring funds using Feather during that time.
Cause
On August 29, 2021, I committed a patch titled ‘Output distribution checks’ to Feather’s fork of the core Monero wallet library. This patch was first included in Feather beta-9, which was released on September 16, 2021.
The purpose of this patch was to provide better mitigations against an attack known as “output distribution poisoning”.
The output distribution is a histogram of RingCT outputs and affects how the wallet selects decoys for rings. When a transaction is constructed, the wallet requests the output distribution from the node it is connected to.
In the attack, a malicious remote node manipulates the output distribution in a way that reveals the true spend to the node with a high degree of certainty. One way a node could do this is by pretending there are significantly more outputs on the blockchain than there are in reality. This causes decoys, which are referenced by their global index, to skew towards this ‘unrealistic’ number.
Consider the following set of output indices which represent a ring, for which the wallet requests the associated public keys from the node:
{99655570, 50001410564, 50001585151, 50001818442, 50001853725, ...}
The node can clearly tell that the first output is the true spend, because it is the only ‘real’ output that exists on the blockchain.
This could allow the node to associate an output with an IP address. Note that, by default, Feather constructs transactions over Tor, and so the only information a node would learn is that “someone, using Tor, is currently trying to spend this output”. By default, Feather connects to a node from a list of nodes operated by known members of the community. If a node from this list was reported to be malicious, it can quickly be removed and the operator shunned.
In this naive approach, the transaction would be rejected by the network because the ring contains invalid indices. The user would receive an error message upon broadcasting the transaction and promptly switch to a different node.
A more sophisticated attacker could present the output distribution in a way where decoy selection is skewed such that the true spend is detectable, but does not result in an invalid transaction.
For instance, this transaction was constructed using a manipulated output distribution. Can you determine what the true spend is? Notice that all ring members are older than 1y 200d except for one 6-day-old output. Unless the user checks the ring on a block explorer and knows what to look out for, they would not notice that their transactions are being fingerprinted.
Even subtler manipulation may give the malicious node only a statistical edge to guess the true spend, but not noticeably fingerprint the transaction on-chain to a casual observer.
The patch attempted to mitigate this attack with two checks:
- It hashes the output distribution returned by a node up until a checkpoint height and compares it against a hardcoded hash. If the hashes don’t match, an error is returned. This prevents any tampering with the distribution before the check-pointed height.
- It checks if the total number of outputs in the distribution does not exceed a predefined limit. This ‘sanity check’ is what ultimately caused transaction construction to fail for everyone when the real number of outputs on the blockchain exceeded this limit.
Upon further review, the first check appears to be an effective measure, as long as it is updated with each release. It limits how much an attacker is able to skew decoy selection. The second check appears to be ineffective, as an informed attacker could still skew the distribution to just below the limit. It would only have caught an attacker that was unaware of the limit.
I initially stated that “a large number of outputs were added last month in a spam attack”, believing the patch was a more recent invention and thought the spam attack had contributed more significantly to expediting the timeline. After gathering the details, I found that the attack only contributed about 2.5 months' worth of outputs to the chain. Moreover, the possibility of such an attack should have been taken into account when considering if was a good idea to impose any such limit in the first place.
- At the time of the patch (Aug 2021) roughly 48.8 million RingCT outputs existed on the Monero blockchain. The limit was set to 100 million.
- The limit and the hardcoded hash were never updated from their initial values.
- By March 3, 2024, at the start of the March spam attack, the number of RingCT outputs on the Monero blockchain had already grown to 90.8 million.
- According to research by Rucknium, the spam attack added about 4.62 or 4.71 million outputs depending on which definition is used for the spam transactions.
- Updating the limit or hardcoded hash was not documented in the release procedure or maintenance priority and the value was not actively monitored. These documents were added precisely to prevent something like this from happening, but were only introduced in Jan 2023. By then, the existence of the patch must not have been top of mind.
- On April 28, 2024, block 3137429 was mined which pushed the number of RingCT outputs over the 100 million limit, triggering the sanity check to fail during transaction construction.
Plans to clean up Feather’s patchset with the goal of “upstreaming as much as possible” were on the agenda. I believe I would have removed the limit if I had worked on this sooner, however this obviously did not happen before the limit was reached. Following the CCS hack, I prioritised work to help ensure the continuity of the CCS, which included finalising support for offline transaction signing with animated QR codes and ongoing work to integrate multisig. This lead to delays in maintenance work.
I conclude that the sanity check should not have been added, and that my failure to properly document, monitor, and maintain the patch ultimately lead to the denial of service.
Response Timeline
2.6.6
20:40 - User miracloe joins the irc channel and is the first person to report that they encountered the error message.
20:46 - I am able to reproduce the error message by attempting to send a test transaction.
To prevent this from happening in the future, the sanity check is removed.
21:41 - The 2.6.6 release is tagged and building begins.
00:04 - The builds are finished and transferred to the release signing machine.
00:13 - Builds are signed and uploading begins.
01:15 - Uploading is finished and the release is available on the site and in the built-in updater.
| Report ➛ Tag | Tag ➛ Release | Report ➛ Release |
|---|---|---|
| 1h 1m | 3h 34m | 4h 35m |
‘Report to Tag’ is the amount of time it took to reproduce, debug and fix the issue.
‘Tag to Release’ is the amount of time it took to release the update, which includes building, signing, and uploading the release artifacts and updating the website.
For most users this concluded the wait, others had to wait until 2.6.7.
2.6.7
01:49 - User rayven123 reports on irc they are unable to open 2.6.6 on Tails 5.
01:57 - I am able to reproduce the issue by attempting to open 2.6.6 on Tails 5.
This problem turned out to be related to a compiler upgrade, and was unrelated to the fix for the output distribution issue. It had existed in the master branch since March 18, but went unnoticed because the issue did not affect my development machine.
Since all versions prior to 2.6.5 were no longer able to send transactions and 2.6.6 did not run on some Linux machines, another release was needed.
During this period several other users reported that they are unable to start 2.6.6 on various Linux distributions, including Whonix and Fedora 40. Another user reported an issue with multi-destination transactions, which took a while to debug, but was ultimately unrelated to the release.
04:37 - The 2.6.7 release is tagged and building begins.
04:50 - Exhausted, I announce that I’m going to head off to get a few hours of sleep.
08:18 - I wake up, and begin uploading builds.
08:48 - The 2.6.7 release is now available on the site and in the built-in updater.
| Report ➛ Tag | Tag ➛ Release | Report ➛ Release |
|---|---|---|
| 2h 48m | 4h 11m | 6h 59m |
Verifying reproducibility post-release
For typical releases, at least two people must submit a signed list of hashes, known as an attestation. This is done to verify that builds are reproducible. If the release is not reproducible, the release process can’t continue; all sources of nondeterminism must be removed and new release must be tagged.
For an emergency release, there is no time to wait for attestations from multiple people. The requirement was lifted for 2.6.6 and 2.6.7.
Luckily, both releases were verified to be reproducible post-release. At the time of writing, 2.6.6 was built by plowsof and me, and 2.6.7 was built by plowsof, MoneroArbo and me, with all hashes matching.
This begs the question as to what would have happened if the builds turned out to be non-reproducible post-release.
In simple cases, like where nondeterminism is trivially attributable to a benign source like an embedded timestamp, an erratum may be published in ERRATA.md. This document was introduced after 2.6.5, which contained an issue with the attestation script.
To describe the defect, a tool like diffoscope may be used to show the binary difference between two builds. This gives verifiers confidence that the release was built from its source code.
If the binary diff is too complex to describe in an erratum, a warning must be issued and the release must be pulled immediately after a new version is available.
Lessons learned
On sanity checks
The main takeaway is to never add sanity checks that may fail at some unknown time in the future, especially when that could prevent essential wallet functionality from working properly. To my knowledge, there are no checks like that in the latest version.
While this was not the intent of the sanity check, I do think it may be useful to have a built-in ‘expiration date’ for a release. Newer releases include bug fixes, improve privacy and security, and patch vulnerabilities (in Feather, Monero, or any of its statically linked dependencies). It is important that users keep the software up-to-date.
A warning could be shown if a fixed amount of time (e.g. 1 year) has passed since the release and prompt the user to consider updating. The user could choose to hide the warning, and continue using the wallet if they do not want to update for whatever reason.
On emergency releases
This was the first emergency release in Feather’s history.
Emergency releases are reserved for two scenarios:
- A critical vulnerability that could result in a loss of funds.
- A denial of service of essential wallet functionality (sending and receiving) that affects the latest Feather version on at least one major platform.
Occasionally, there has been a need for ‘fast’ releases. Like, 2.6.3 which fixed an issue that prevented Feather from running properly on Tails 6, or 2.6.4 which fixed automatic fee adjustment during the aforementioned spam attack. In both cases, there was some sense of urgency, but the problems were not severe enough to qualify for an emergency release. Fast releases must still adhere to the release procedure, but may be announced ‘on the fly’ when a situation arises.
An emergency release should branch off from the previous release, and only include the critical fix and potentially other important fixes that were pending for the next release.
This minimizes the chance of introducing new bugs. Typical releases are tested before they are tagged to check if the complete set of changes does not create any new issues. While this must also happen for an emergency release to ensure that the fix actually works, there is not enough time to test all pending changes.
In case any build system changes or packages updates were pending to go into the next release, it also minimizes the chance of introducing nondeterminism into the build process.
Regrettably, I made the decision to base the 2.6.6 emergency release on master, instead of 2.6.5. The 2.6.6 release contained 20 commits since 2.6.5, which other than the critical fix were all pending changes for the next release and included build system changes, low to medium priority fixes, and a new feature that I had recently tested.
The critical fix removed three lines of code (including an empty line and a comment). Had only this fix been included, it would also have been easier for others to compare the source code of 2.6.5 and 2.6.6 and be confident that the emergency release wasn’t used as an opportunity to introduce malicious code into the source code.
The build system changes ended up causing the bug that resulted in the need for a second emergency release and could also have easily caused nondeterminism. Should an emergency release be needed in the future, I will not make this mistake again. On the upside, much requested fee changes made it into 2.6.6.
On the release procedure
Let’s break down how long each stage of the release procedure for 2.6.6 took and discuss ways in which this it can be optimized.
| Building | Signing | Uploading | Total |
|---|---|---|---|
| 2h 23m | 0h 9m | 1h 2m | 3h 34m |

The total size of release artifacts for any release is about 1000 MB. Signed hashlists and signatures only make up 150 KB of that.
To maintain anonymity, releases are uploaded over Tor to the webserver from a dedicated “upload machine”. Uploading a gigabyte worth of data over Tor can take a while and upload speed can vary widely. The 2.6.6 release took over an hour to upload, and the 2.6.7 release ‘only’ took 30 minutes. If the Tor network has degraded performance, uploading a release could take hours or days. Clearly, in scenarios where time to release must be minimized, any added wait is undesirable.
When a release is tagged, a GitHub CI job begins building it. Thanks to reproducible builds, the artifacts produced by GitHub will match local builds bit-by-bit (unless a source of non-determinism was introduced).
It took the CI job 2h 20m to finish the builds, which is roughly the same amount of time it takes me to build locally. Despite the low thread count available to GitHub runners and lack of caching (due to storage constraints), it greatly benefits from parallelization by building each target on a different runner. In contrast, local builds are sequential, meaning one target is built after another. Any moment where the local build process is not able to utilize all available cores (e.g. during package configure stages) it loses out to parallelized builds.
To decrease the time it takes to complete the upload stage of the release process, only the signed hashlists and signatures could be uploaded to the webserver. It can then fetch the artifacts from GitHub and verify the signatures. Since it can do this over clearnet, this is expected to take only a minute or two. This would have saved nearly an hour on the time it took to get the 2.6.6 release out.
A lower bound of 2h 20m for Tag to Release still isn’t ideal. Breaking down the CI run for the slowest target, we find that time is spent on the following tasks:
| Step | Time | Cacheable |
|---|---|---|
| Setting up the runner | 0h 2m | No |
| Setting up Guix | 0h 12m | Maybe |
| Building Guix derivations | 1h 00m | Yes |
Building depends packages |
0h 48m | Yes |
| Building Feather | 0h 18m | No |
Most time is spent re-building stuff that could have been cached. We should be able to fit all cached data within GitHub’s 10 GB cache limit, if we only keep caches for the latest tag. With caching, the lower bound becomes 20 - 44 minutes.
We can’t rely on GitHub solely for builds, so a way to parallelise local builds must also be developed. Typical releases would also benefit from this.
On communication
Information about the incident could have been communicated to users more effectively.
Here is where information could have been posted:
- A notice on the website / RSS feed
- The description of the irc / matrix channel
- An issue on GitHub
- A post on monero.town and X
I did not have an automated way to quickly post an update across these channels and did not want to detract time from getting the release out, so I did not post an update everywhere. A script on the “upload machine” could have taken care of posting a short message to all channels, so I will work to set that up.
Thanks to SummerBreeze for creating a thread on monero.town and x011 for creating an issue on GitHub during the incident.
2.6.7 changelog (2024-04-29)
- Fixes startup issues on some Linux distributions.
2.6.6 changelog (2024-04-28)
This is an emergency release to fix “Internal Error: Unrealistic number of outputs in output distribution” that prevented any transactions from being constructed.
The number of outputs on the blockchain exceeds a safety limit present in version 2.6.5 and below that was meant to mitigate output distribution poisoning. This caused a sanity check to fail during transaction construction.
Update your wallet to version 2.6.6 or later to resolve this issue.
Fixes and improvements
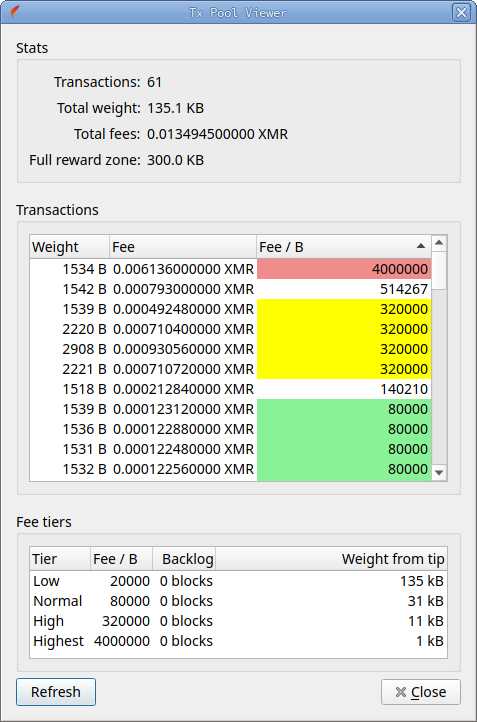
- added a transaction pool viewer (Tools -> Tx Pool Viewer)

- send: options to enable ‘manual fee-tier selection’ and ‘subtract fee from amount’ were added to the transactions tab in the settings.

-
send: in automatic fee mode, an option to use the ‘High’ fee-tier is presented if there is a backlog of 3 or more blocks at the ‘Normal’ fee-tier
-
send: removed unnecessary RPC calls, which slightly speeds up construction on slow networks
-
trezor: disabled bridge transport, improved error messages
-
trezor: selecting an address in the Receive tab no longer requires device communication
-
windows: more mitigations against false-positive AV detections
-
fixed a potential crash on exit
Maintenance
- GCC 12.3 is now used to build Linux and Windows targets, up from 10.5
- updated Qt to 6.7.0
2.6.5 changelog (2024-03-14)
Fixes and improvements
- fixed an issue that could prevent Feather from closing
- wizard: allow restoring legacy seeds that miss the checksum word
- history: fix amount calculation for multi-destination txes that have multiple change outputs
- history: added an option to remove failed transactions
- send: improve the help text for certain rpc errors
- coins: fix automatic fee adjustment for selected transfers
- macOS: fixed an issue that prevented Feather from asking for camera permissions
Maintenance
- updated Monero to v0.18.3.3
2.6.4 changelog (2024-03-10)
Fixes and improvements
- send: automatic fee adjustment works now
- wizard: add a legacy seed recovery dialog
- history: fix transaction sort order in csv export
- receive: sanity check ownership of each generated address
- windows: mitigate false-positive AV detections caused by embedded ‘cryptonight’ strings
- add more nodes to the default list
Maintenance
- updated Monero to v0.18.3.2
- updated Tor to 0.4.8.10
2.6.3 changelog (2024-02-28)
This release fixes Tails detection. Previous releases may be unable to connect to nodes and default to saving wallet files outside the persistent storage on Tails 6.0 or higher.
Fixes and improvements
- send: allow pasting monero: uris in the pay to field
- settings: allow configuring block explorer urls
- statusbar: add wallet height tooltip
- history: sort by blockheight for date ordering
- history: set default description to “Coinbase” for mining outputs
- history: fix values of copied amounts
- tray: don’t notify when wallet is locked
- coin control: don’t allow selecting unspendable coins
- set focus to password entry when shown
- about: add website .torify.net address
- adv. tx conf.: allow copying values from inputs/outpus tables
- the reddit plugin was removed
Maintenance
- Updated Qt to 6.6.2
- Updated OpenSSL to 3.2.1
2.6.2 changelog (2024-01-03)
Fixes and small suggestions.
- locking the wallet should no longer cause the connection status to incorrectly state it is disconnected
- wallet synchronization status is now shown on the lock screen
- contacts: adding a new contact will no longer fail if the address and name are entered the wrong box
- history: added an option to show the full txid
- history: the default tx description for incoming payments is now the associated subaddress label
- coins: the default coin label is now the description of the tx that created the output
- trezor suite may cause feather to fail to acquire the device. an error message now informs the user to close trezor suite.
- send: added an option to manually broadcast a transaction when sending a tx failed
- macos: scanner should now show a warning if it does not have permission to access the camera
- setting a password for a view-only wallet created from a spendable wallet now requires entering the password twice
- docs: reddit was removed from the list of support channels. my account is still suspended for unknown reasons
- build: removed an unnecessary file from the windows installer .zip release artifact
- build: fixed an issue that caused builds without scanner support to fail
- build: vendored bc-ur (for now) because of lack of availability in package managers causing issues for development builds
- depends: updated boost to 1.84.0
2.6.1 changelog (2023-12-16)
Bugfix release:
- macOS: fixed a crash that could trigger after opening a wallet
- macOS: disconnecting a ledger during tx construction should no longer lead to UI unresponsiveness
- send: transactions that failed to submit to a node can now be retried
- airgapped signing: view-only details QR code is now compatible with ANONERO
- docs: images should now show up in the built-in documentation browser
- depends: updated zxing-*****p to 2.2.1
2.6.0 changelog (2023-12-09)
Airgapped signing with animated QR codes

This release features a major overhaul to the offline transaction signing UX and introduces animated QR codes as a way to quickly transfer data between devices.
The offline wallet has a new UI that takes away the clutter and shows only what’s relevant to airgapped signing.
You will no longer need to click through menus to import / export files. A wizard was added that guides you through the process step by step. You can choose whether to transfer using files or animated QR codes.

Feather uses Blockchain Common’s Uniform Resources library (UR for short) to chop up and encode binary data (such as an encrypted unsigned transaction) into URIs, which can then be presented as animated QR codes.

On the other side, a webcam can be used to scan the QR codes, which can then be reconstructed into the original binary data. Scanning can happen out of order, so if it ‘misses’ a QR it can pick it up in the next cycle. You just keep scanning until the progress bar fills up to 100%.
By default, each QR translates to roughly ~50 bytes of binary data and animates at 12.5 fps. This was chosen conservatively to allow even the worst webcams I tested with to scan easily. A signed 2-in/2-out transaction (~2.2 kb) takes roughly 3.4 seconds to display all fragments. With a decent webcam and a big enough screen, you can tweak these values to take as little as 280 ms. You can’t plug in a flash drive that fast.
Key images are kept in sync as you spend, so you will only infrequently have to synchronize them manually. Typically, this is only required when you send your first transaction or don’t have enough outputs with known key images to construct a transaction. When you do need to synchronize, the wizard will guide you through the two extra steps.
A lot of effort went into making the process less prone to breakage, while keeping compatibility with other wallets. You shouldn’t encounter issues when restoring from seed, wiping your wallet cache, using a partially restored view-only wallet, or switching to a different view-only wallet file.
Monero’s current binary format for inputs, outputs, and (un)signed transactions makes implicit assumptions about the state of the wallet that imports the data, which works if everything is done correctly, but is very brittle in practice.
To work around this, the offline wallet no longer stores imported outputs or transaction records. It can’t keep an accurate history because it is not connected to a node (and should never be), so why even try. This allows us take a more functional approach to airgapped signing. Given a set of outputs, it returns the associated key images. Given a unsigned transaction, it returns a signed transaction (if the user approves).
To learn how to set up an airgapped wallet and spend from it, follow the guide here.
A special thanks to r4v3r23 from ANONERO, an airgapped wallet for Android that implements UR, for brainstorming ideas and helping test compatibility.
Plugins

This release introduces a preliminary plugin system. Many features that are not essential wallet functions that were present in the previous release are now plugins.
To manage which plugins are enabled, go to Settings → Plugins. Currently, all plugins are enabled by default. If a plugin is disabled, its code is never instantiated.
The Home tab was divided into 5 plugins: Crowdfunding, Bounties, Reddit, Revuo and Tickers. If none of those plugins are enabled, the Home tab is removed completely. It won’t even show up under ‘View’.
Similarly, disabling the LocalMonero plugin removes the Exchanges tab. Other tabs that are now plugins are Calc and Mining.
The plugin system is a notable improvement over the current state:
- It may serve as a mechanism to introduce experimental features that we’d to like collect feedback and iterate on, before considering if they’re useful enough to enable by default. Or allow us to ship niche features that are useful only to a small subset of users, without complicating the default UI.
- Users that enjoy a more minimal experience now have the option to completely disable features they don’t use. It was already possible to “Hide” optional features, but this goes a step further by preventing the associated code from being executed.
- (Individual) plugins can easily be disabled during build time, in which case they will simply be absent from the app. This opens the possibility for a “minimal” Feather distribution in the future.
- Should a plugin cease to be relevant, it can be removed without requiring changes to other parts of the code.
Plugins can’t (currently) be loaded dynamically. This means that there is no plugins folder to drop new plugins in. Only plugins that exist in Feather’s source tree and that are included during the build process are available in the app.
There is an ongoing discussion on whether to allow third-party plugins or exchange integrations. I would like to hear your feedback on this. I will not accept new plugins until the plugin interface is finalized and we reach rough consensus on how to move forward on this.
Additional entropy from dice rolls

You can now optionally use dice rolls or coins flips to generate additional entropy for the creation of a Polyseed.
For usage information, check the documentation.
Receive tab

The Receive tab has a new options menu. It is accessible from the settings icon next to the search bar or by right-clicking the table header. Options are now persisted and the index and label columns can now be hidden.
You can now Pin an address to move it to the top of the table and keep it visible regardless of filter settings. This may be useful to keep a quick reference of an address that was given out to an exchange or a friend, or as a reminder to check up on expected payments.
Additions
- The CCS tab was renamed to “Crowdfunding”. It now shows active funding campaigns from MAGIC Monero Fund in addition to the CCS. (Thanks to Rucknium for working on the API.)
- You can now configure the tickers shown in the Tickers plugin. To do this, select the Tickers plugin in the settings and click Configure.
- Added an option to obscure the seed entry when restoring a seed.
- Added Trezor Safe 3 to the list of supported hardware devices.
- The tables in the Bounties and Reddit plugins are now sortable.
- Improved error messages when spendable balance is insufficient to pay for the transaction fee.
Bugfixes
- Failing to enter a valid password when opening a wallet should no longer prevent the program from exiting completely
- Fixed an issue that could prevent icons in table views from showing on Windows
- Fixed an issue that triggered a crash when Scan was pressed on the Send tab on Windows
- The Flatpak release should no longer fail to start the embedded Tor binary
- Feather should no longer fail to connect to the bundled Tor daemon after a crash
- Desktop files created with AppImage builds should now write the correct application path
- Fixed an edge-case where partial view-only wallet restores could show transaction history entries with unrealistic balance mutations
- Reduced the chance of transaction construction failing due to network issues in the later stages of construction
Maintenance
- Updated OpenSSL to 3.2.0
- Updated Qt to 6.6.1
- Updated Tor to 0.4.8.9
How to help verify reproducible builds
Would you like to help users reach greater confidence that Feather is bit-by-bit reproducible across a wide range of systems? And, do you have access to a decent Linux machine?
Here is all you need to do to get builds running:
System requirements
OS : any GNU/Linux distribution
Storage : 60 GB free
Cores : 4 or higher (recommended)
Memory : 2 GB per thread
You will also need a GitHub account and a GPG key to attest your builds.
Install Guix
$ apt install guix
(or the equivalent for your package manager)
Clone Feather
$ git clone https://github.com/feather-wallet/feather.git
$ cd feather
$ git checkout 2.6.0
(Don’t forget to checkout the version you want to build!)
Run the builds
$ ./contrib/guix/guix-build
This may take several hours depending on the speed of your *****U.
Attest your build outputs
Follow the steps here: https://paste.debian.net/plainh/2457c02c
If you get stuck on any step or your hashes don’t match, please let us know. Joining the Matrix/irc channel is best for this.
A special thanks to MoneroArbo and plowsof for submitting their signed build hashes before the release.
2.5.2 changelog (2023-10-19)
Documentation browser

Feather now has an offline documentation browser. It is accessible by pressing the ‘Help’ button in the wizard or by going to Help → Documentation.
Enter a keyword in the search bar to filter the list of articles and highlight matches.
If you spot an error or can’t find what you’re looking for, consider opening an issue on the feather-docs repo.
Improved error messages
In some cases error messages provide too little information to be helpful or too much and it becomes confusing. I recently came across this post, which highlighted this issue and prompted me to make a change.
Most error messages bubble up from the wallet library. It doesn’t shy away from using internal terminology and often includes unnecessary information, like references to the source code. That’s useful for developers, but not so much for users trying to understand what went wrong and what to do about it.
To address this, many error messages were rewritten for clarity and made more actionable. They should now adhere to a format that aims to answer the following questions:
- What action went wrong?
- Why did it go wrong?
- [What can I do about it?]
- [Where can I learn more?]
For instance, trying to send a transaction when the wallet has not yet finished synchronizing now shows:

Pressing ‘Help’ opens the docs browser with more information about wallet synchronization to help a curious user understand why the wallet must be synchronized in order to send a transaction.
Writing good documentation for every case is very much a work in progress. If you see a confusing error message, consider reporting it.
Seed recovery

A seed recovery tool was added that can help recover damaged or partial Polyseeds.
Occasionally, I get an e-mail from someone trying to restore a wallet from a backup seed, but they can’t make out what some of the words are. Bad handwriting, a coffee stain, a picture that was badly cropped, etc. Too much information is missing to make it practical to go through by hand, but not enough to make recovery computationally infeasible.
The tool allows you to enter all information you do have about the seed phrase. Regex is supported for partial words. It will then iterate over all possible phrases given the (whole, partial or blank) words provided. Polyseeds include a 11-bit checksum, so only a subset of seed phrases are valid. An address associated with the wallet can optionally be provided to automatically check if any of the valid phrases produce a wallet that contains the address.
For information on how to access and use the tool, see the docs here.
Time machine bump
Feather releases are bootstrappable. This means that the tools used to build Feather are built from source, and the tools that build those tools are too, and the tools that build those tools are too, and so forth.
But surely, this can’t go on forever and something can’t come from nothing. At the root of the package graph sits a binary seed, a minimal set of binaries that can’t be built from source. This used to be the ~60 MB Further Reduced Binary Seed.
With this release, our Guix time-machine was updated to a commit on May 15. Feather builds now benefit from the Full-Source Bootstrap. The root of the package graph is now a heavily annotated 357-byte program, known as hex0.
It’s source code all the way down! Every step of the build process is auditable and we do not have to trust someone’s potentially malicious binaries.
One important caveat is that while all packages are built from source, the driver that is used to build the initial packages is not. Eliminating this driver is the next step in bootstrappable builds.
(Work is underway to bring bootstrappable builds to the core Monero repo.)
Release attestation
Feather releases are reproducible. Anyone with a x64 Linux machine and Guix (the package manager) installed can create a bit-for-bit identical copy of all release artefacts by running a single command.
The only way to verify that a release is in fact reproducible is to build it multiple times, on different systems. While builds are done inside a container with a normalized build environment, non-determinism can still creep in from (among other things) properties of the build machine, like the kernel, *****U architecture or the bind-mounted filesystem. The more diverse the set of machines the software is built on, the more confident we can be that there are no undocumented requirements for reproduction.
This release adds release attestation, sometimes called verified reproduction. If you’re familiar with Monero’s reproducible build process, this works the same way as gitian.sigs. Anyone can build Feather, sign the hashes of the outputs and submit it to a common repository. The hashes can then be compared to verify that the builds are reproducible.
With release attestation, users that don’t build from source can be more confident that releases are reproducible because multiple contributors will have independently produced identical binaries. Should non-determinism occur, it can be fixed before a release.
A special thanks to /u/MoneroArbo for helping verify reproduction of this release. Their first build (for 2.5.0) revealed an undocumented assumption about the host’s umask, which leaks into the container and can introduce non-determinism when newly created files are archived.
If you would like to help verify this release, follow the instructions here to build Feather and create an attestation. We recommend using a machine with at least 8 cores and 32 GB of memory, though this is not a requirement.
Official Flatpak release
Feather now has an official Flatpak.
A lot of effort has gone into making sure that it has the same build security guarantees as our other releases. The Flatpak is bootstrappable and reproducible. It has no dependency on any third-party runtime and does not require trust in Flathub’s infrastructure.
The repository is hosted on featherwallet.org and all commits are signed with our release signing key, allowing users to verify the authenticity.
It’s also tiny compared to most Flatpaks, weighing in at only ~30 MB (compressed). That’s the (empty) runtime + application. It only includes files that are necessary for the application to run, not even a shell or coreutils.
For more information about the considerations that went into this, see my post here.
To install the official Flatpak, simply run:
flatpak install --from https://featherwallet.org
and follow the instructions here to verify your download.
Bugfixes and improvements
- Feather now starts exactly one second faster
- Receive: added an option to show change addresses
- Wizard: automatically select the first wallet, if it exists
- Ledger: private viewkey is now available in Wallet -> Keys
- Node username/password are no longer forgotten upon restart
- Mining: allow adding additional command line options
- All files can now be selecting when importing (un)signed transactions
- Windows installer will now abort if it runs on an unsupported version of the OS
- Fixed an issue that could cause the History tab not to update on an incoming transaction
- Send: clear donate description if address was changed
- Fixed an issue that could lead to a crash
- Fixed a build issue on musl platforms
- Some cosmetic improvements for macOS
Other changes
Many (statically linked) dependencies were updated in this release. Including Monero to v0.18.3.1, Qt to 6.6.0, OpenSSL to 3.1.3, Boost to 1.83.0, and Tor to 0.4.7.15.
In anticipation of animated QR codes for offline transaction signing, the ZBar library, used for QR code scanning, was replaced with the faster and actively maintained ZXing-*****p library.
Our type2 AppImage runtime was updated to the latest version and now uses fuse3.
This does not resolve an issue with AppImageLauncher, which throws an error when trying to install the AppImage. Users are recommended to uninstall AppImageLauncher or remove the .AppImageextension from the file.
This release drops support for Qt 5, which has been EOL since May 26 and no longer receives public security updates. The minimum required Qt version to build Feather is now 6.3. Official releases already switched to Qt 6 in January.
Two documents were added to the repo:
- RELEASE.md describes the release process.
- MAINTENANCE.md outlines maintenance priorities and development goals.
Check out the last document if you’re interested in learning more about where the project is headed.
macOS codesigning requirements
It is becoming increasingly difficult to ship non-codesigned applications for macOS.
Apps for Apple Silicon that target macOS 10.15 or later will not start if downloaded over the internet, even if they are ad-hoc codesigned which is what Feather does now.
A workaround involves removing an xattr using the terminal, but this is not something we can reasonably ask from non-technical users.
It is unfortunately not possible to obtain an Apple-issued Developer ID certificate without jeopardising my identity, which is not something I feel comfortable doing at this time.
If you are able to obtain an Apple-issued codesigning certificate and are willing to grant me access to it, please contact [email protected]. Any expenses and time incurred will be compensated in XMR.
Note: while current releases are not “codesigned” according to Apple’s definition, all releases are GPG signed with our release signing key. To verify the authenticity of a release, follow the instructions in the installation guide.
2.4.9 changelog (includes security fixes) (2023-05-24)
Security Advisory
This release includes a fix for a recently disclosed decoy selection vulnerability that was present in the Monero codebase before v0.18.2.2. For more details, see: https://github.com/monero-project/monero/issues/8872
Users are recommended to update as soon as possible.
- Updated Monero to v0.18.2.2
- Updated expat to 2.5.0
- Updated unbound to 1.17.1
- Updated icu4c to 73.1
- Updated protobuf to 3.20.3
- Patched Qt for CVE-2023-{32573,32762,32763}
- Patched OpenSSL for CVE-2023-{0464,0465,0466,1255}
- wizard: preserve words when switching to a different seed type
- wizard: macos: fixed inverted buttons on the seed warning dialog
Full list of changes: https://github.com/feather-wallet/feather/compare/2.4.5...2.4.9
2.4.5 changelog (2023-04-05)
- New app icon design
- Native Apple Silicon builds are now available
- AppImage: Switched from lzma compression to zstd; size reduction, faster startup time
- AppImage: fuse2 is now linked statically in the AppImage runtime
- AppImage: XCB libs are now included in ARM(64) and RISC-V AppImages
- Updated Qt to 6.5.0
- Build system improvements
Full list of changes: https://github.com/feather-wallet/feather/compare/2.4.4...2.4.5
2.4.4 changelog (2023-03-23)
- RISC-V builds are now available
- Fixed an issue that caused importing keyimages to take longer than necessary
- It is now possible to select any file when importing keyimages or outputs
- Settings: the proxy host should no longer reset back to localhost when the settings dialog is reopened
- Build system improvements
2.4.3 changelog (2023-03-15)
Note: includes changes from 2.4.2, which was not released due to a reproducibility defect.
- AppImages for Tails / Whonix / Prestium no longer bundle a Tor binary, shaving ~3 MB off the binary size
- the built-in updater should now work on macOS
- macOS builds are once again shipped as application bundles, instead of .DMG files (due to superior UX and smaller download size)
- Receive: added a column that shows the subaddress index
- opening more than 3 wallets will no longer cause the application to freeze
- new wallets should now always start syncing from the current blockheight
- Linux: typing composed characters (e.g. ‘e -> é) now works
- nodes: the IP range 100.64/10 is now considered local
- DebugInfo: added Proxy information
- stack trace: added version and OS info to log output
- Fixed a few issues that could cause application crashes
- Fixed a build issue on Qt 5
- Update unbound to 1.15.0
- Update polyseed to 2.0.0
- Update OpenSSL to 3.0.8
- Linux: minimum glibc version is now 2.27 (this drops support for Ubuntu 16.04)
2.4.1 changelog (2023-02-15)
Bugfixes
- macOS: fixed a potential crash on exit
- proxy: “only allow connections to onion services” no longer applies to local nodes
- send: don’t show fiat conversion using cached variable if websocket is disabled
2.4.0 changelog (2023-02-12)
Settings screen redesign
This release adds a few new options to the settings, with more planned in future releases. The old UI would have become a bit too cluttered, so settings are now conveniently categorized into Appearance, Network, Storage, Display, Transactions and Misc.
Note that Feather ships with reasonable defaults and most users do not need to mess with the settings at all. However, if you have a specific threat model, it should now be easier to find settings relevant to your concern.
- added an option to lock the wallet when the window is minimized
- added an option to disable writing stack traces to disk
- added an option to hide update notifications
- added an option to not write a list of recently opened wallets to config file
- all available fiat currencies should now be selectable as the preferred fiat currency
- the log level can now be configured
- the log file can now be opened from within the application
- the node tab UI should now be less cluttered
- changing a setting when multiple wallets are open now affects all wallets immediately
- the settings dialog can now be accessed from the main menu (before a wallet is opened)
Proxy settings
A proxy tab was added to the settings. This tab replaces the current Tor Info dialog, consolidating all network related settings into one place. Feather can be configured to route traffic over Tor, I2P, socks5 or no proxy at all.
By default, Feather will still route most traffic over Tor. But, if you’re unable to connect to the Tor network or would rather use a different proxy, you have the option to change the settings before any network connections are made when Feather is started for the first time (or after).
I2P support
With the new Proxy tab comes the option to configure Feather to route all traffic over I2P.
Feather is now “I2P-aware” and comes with a built-in list of I2P nodes. All wallet functionality, including the websocket connection (if enabled) as well as the built-in updater will continue to work if you switch to I2P.
Instructions on how to set up I2P and configure Feather can be found in the documentation.
The I2P network is currently under a DDoS attack and is very slow as a result. Expect very slow synchronization for now.
The site is now available on I2P as well: https://rwzulgcql2y3n6os2jhmhg6un2m33rylazfnzhf56likav47aylq.b32.i2p
Feather now supports Prestium, a privacy focused, I2P based live operating system. In an upcoming release Feather will be bundled with Prestium. For now, you can download the AppImage for Linux. Proxy settings are autoconfigured to use I2P when Feather is started for the first time on Prestium.
Other changes:
- updater: you can now manually check for updates via ‘Help -> Check for updates’. This will allow you to update Feather to the latest version, even if the update is not yet advertised to clients. (note: the updater is currently disabled on macOS.)
- statusbar: fixed an issue that could cause Feather to report that it was “Disconnected” when it was in fact “Connecting to a node”
- libwallet: transactions that were broadcast using a tx pusher will now show up in the history as soon as they reach the mempool, rather than once they have at least one confirmation
- windows: clicking the button to open the wallet directory in ‘Wallet -> Information’ will now actually open the wallet directory
- mac: the version number should now be embedded in the application bundle
- bounties: the bounty amount is no longer displayed twice
- upgraded OpenSSL to 1.1.1t
- upgraded Tor to 0.4.7.13
2.3.0 changelog (2023-01-31)
- verify tx proof: added option to verify a payment using the transaction secret key
- wizard: added option to set subaddress lookahead when restoring from device, seed, keys (thanks labrocca for the issue)
- wizard: added option to override embedded wallet creation date for 14/16-word seeds
- wizard: allow restoring deterministic wallet from private spend key (thanks 4Lj2jEe3ilXl5r for the suggestion)
- locking: pressing Ctrl+L will now immediately lock the wallet (thanks chaserene, maltfield for the issues)
- locking: (auto)-locking the wallet will no longer bring Feather into the foreground (^)
- locking: (auto)-locking the wallet will now close all opened dialogs (^)
- linux: in the event of a crash, feather will output a stack trace to the console, write it to disk and attempt to restart itself to show a dialog with the trace and some info (thanks George for reporting a crash)
- portable mode: paths to recently opened wallets now saved relative to the application (thanks GenericName9173 for the bug report)
- account switcher: fixed a sorting and display issue (thanks lalanza808, chaserene, erembax for the report)
- account switcher: sort order is kept during session (^)
- ledger: no longer allow copying the encrypted transaction key to clipboard (thanks mrmonero for the report)
- websocket: fixed a issue that could cause a connection delay
- tx broadcast: dialog is now closed on successful broadcast (thanks chaserene for the report)
- windows: fixed an issue that rendered text unreadable when windows dark mode is activated (thanks johnbennson, is_Mehrdad for the report)
- xmrig: don’t hardcode the donate-level (thanks MorvickLeb for the issue)
- fixed an incorrectly named folder in the signed source tarball
- updated Monero to v0.18.1.2
Thanks lovera for testing Feather on ARM64, and all the lovely people hanging out in #feather:monero.social.
PGP verification guides are now available for all supported operating systems (thanks maltfield for the issue):
See the sidebar in the docs for more.
The release signing key is now available in more places for out-of-band verification (^):
https://docs.featherwallet.org/guides/release-signing-key
The built-in updater was not enabled for versions 2.2.x by mistake. Manually download the latest version from https://featherwallet.org/download to upgrade.
2.2.3 changelog (2023-01-13)
- Fixed scaling issues on Windows and Linux
- Fixed an issue that caused Feather to be unable to connect to Trezor devices on macOS
- Minimum macOS version is now 10.14 (down from 10.15)
- (Re)-broadcasting transactions should no longer throw an error (‘Protocol “http” is unknown’)
- Added more default nodes (thanks to lalanza808, plowsof, sgp)
- Settings: added an option to disable notifications (thanks to stig-atle)
- Settings: Updated Reddit frontend list (thanks to piconero, gStart3)
- Settings: added MoneroBlock block explorer (thanks to duggavo)
- Fixed some typos (thanks to rex4539)
Note for macOS users: Before upgrading an existing installation, rename the “feather” app in your Applications folder to “Feather” (capitalized).
2.2.2 changelog (2023-01-06)
Build system changes
This release introduces major changes to Feather’s build system. While this doesn’t affect any user-facing functionality, it does enable faster, more secure releases.
Feather Wallet releases are now bootstrappable. This means that we are able to build our entire toolchain and dependencies from their source code. By leveraging Guix, a reproducible build environment can be set-up on any Linux host in a matter of minutes. The depends build system makes it possible to build for all target platforms from a single machine through cross-compilation. This greatly reduces release engineering overhead and allows for much faster release cycles, which is especially useful for important bug fixes. It also reduces the risk of supply chain attacks, as all dependencies are pinned and upgrades can be thoroughly reviewed. All builds are bit-for-bit reproducible, and all third-party source code can be accessed indefinitely through fallback mechanisms, ensuring that Feather releases remain reproducible.
Additional resources:
- https://github.com/Sjors/nado-book/blob/master/attacks/guix.md
- https://yewtu.be/watch?v=I2iShmUTEl8
- https://reproducible-builds.org/news/2022/05/18/jan-nieuwenhuizen-on-bootrappable-builds-gnu-mes-and-gnu-guix/
New supported platforms
Starting with this release Feather supports Raspberry Pi and Linux ARM64. Support for RISC-V is planned. Linux ARM64 builds aren’t currently listed on the downloads page, but can be found here: https://featherwallet.org/files/releases/
Qt upgrade
Qt was upgraded from 5.15 to 6.4. You may notice some small visual differences compared to the previous version. We’re aware of some text cutoff happening in table headers in dark mode, this will be fixed soon.
macOS release
macOS builds now ship as a .dmg file. The installation instructions were updated to reflect this.
Webcam QR scanner
The webcam QR scanner now works on standalone Linux binaries. On Linux, the scanner no longer depends on GStreamer, but uses V4L2 directly. Considerable changes were made to Qt’s multimedia backend between 5.15 and 6.4, which may have fixed some bugs and introduced others.
Please let us know if you experience any issues with the scanner on this release.
Source tarballs
Signed source tarballs can now be downloaded from the downloads page. If you’re looking to package Feather for your distribution, please hop on #feather:monero.social for guidance.
Windows installer
The installer for Windows was ported from Inno Setup to NSIS. You can run the new installer to upgrade your current Feather installation without uninstalling the old version first.
Hardware wallets on Windows 11
This release fixes an issue that could cause Feather to be unable to access hardware wallets on Windows 11.
2.1.2 changelog (2022-12-20)
(This release is only available for AppImage builds)
Fix issue with embedded version number in previous release.
2.1.1 changelog (2022-12-20)
(This release is only available for AppImage builds)
- Tails: fixes failure to start on Tails 5.8
2.1.0 changelog (2022-08-12)
Notes:
Windows users that installed Feather using the installer should update manually. Download the 2.1.0 installer from featherwallet.org/download and follow the installation procedure like normal.
MacOS builds are now cross-compiled and reproducible. Work on migrating the build system to Guix + depends was expedited due to a persistent issue with native non-static builds. This is a significant change and may inadvertently cause compatibility issues on some versions of macOS. If you were previously able to run Feather but are not able to run 2.1.0, please report it.
All release binaries except macOS were built using Docker. We will gradually phase out Docker builds in favor of bootstrappable Guix builds in future releases after additional testing.
Please note that all Feather versions 1.0.1 and lower will stop working after the August 13 hardfork. Make sure to update your wallet to 2.0.0 or later before contacting support.
Fixes:
- Sweeping or sending all spendable balance to an integrated address should no longer throw an error
- Fixed an issue that could cause the built-in updater to fail to install Feather (Windows installer)
- Importing a transaction should no longer hang the UI
Maintenance:
- Updated Monero to v0.18.1.0
Known issues:
- macOS: the webcam QR scanner is not enabled for this release
2.0.0 changelog (2022-07-08)
This release is ready for the August 13 hardfork.
Features:
- Integrated Polyseed seed scheme
- Coin control: manual input selection
- Settings: new Privacy tab
- Option to disable fetching third-party data
- Option to disable logging to disk
- Option to set inactivity lock timeout
- Option to enable offline mode
- Ledger Nano S+ support
- Home:
- added XMR/BTC price ticker
- added bounties.monero.social tab
- added Revuo Monero tab
Improvements:
- Allow setting seed offset passphrase during wallet creation
- Send: warn on high fee
- Only allow a single instance of Feather to run
- Calc: show a warning if exchange rates are out of date
- Add a fallback websocket node
- libwallet: verify keys before returning address list
- Warn if wallet is non-deterministic
- Require password to open Wallet Cache Debug
- Tails: write files to feather_data instead of .feather
- Send: don’t allow creation of split transactions
- Removed the connection status dialog, clicking the network indicator in the statusbar will now open Settings -> Node
- Portable mode: accept “portable.txt” (without leading dot) to enable portable mode
- Tails/Whonix: connect to non-onion node during wallet synchronization to speed up synchronization
- Importing a transaction no longer requires “loading” it first
Fixes:
- Bundle official Tor executable on Windows (should stop Windows Defender from complaining)
- macOS: fix webcam QR scanner permissions
- Send: allow sending all in fiat mode
- Fixed the inability to send transactions in testnet / stagenet mode
- Home: switching between tabs should no longer have a noticeable delay
- Ensure all files written by Feather in portable mode are written to feather_data (including ringdb)
- Fixed an issue that could cause LocalMonero settings to be ignored
- Fixed an incorrect error message during offline tx signing
Maintenance:
- Build: cross-compiled and reproducible macOS builds / bootstrappable builds (WIP)
- Prepared Feather for the switch to Qt 6
- Updated Tor to 0.4.7.8
- Updated OpenSSL to 1.1.1p
- Updated Qt to v5.15.5
- Removed zeromq dependency
- macOS: allow compiling on ARM64
1.0.1 changelog (2021-11-02)
- Fixed potential crash on macOS
- Fixed an issue that could cause Feather to rapidly reconnect to nodes
1.0.0 changelog (2021-10-29)
- Removed the Beta warning that is shown on first startup
- Opening most dialogs in one window should no longer block input in other windows
- The websocket connection will now be established slightly faster (by 1-2 seconds)
- Transaction history CSV export format was improved
- Users should no longer encounter “Too many transactions requested in restricted mode” errors when the mempool is full
- History: amount shown for incoming transactions no longer includes network fee (thanks to Lyza for the report)
- History: fixed an issue that could cause the Fiat column to show ‘?’
- History: copying fields using the context menu should now be consistent with what is shown in the table
- History: the preferred fiat currency is now always used for the Fiat column (thanks to /u/Megatripolis for the report)
- History: the txid column should no longer disappear after clearing a search
- TxInfo: add button to copy transaction ID
- TxInfo: disable ‘copy tx secret key’ button for incoming transactions
- TxInfo: added a clickable icon to view transaction on block explorer
- Send: warning displayed when multidestination transaction input is invalid now returns correct line numbers
- Send: resolving OpenAlias no longer hangs UI
- TxConfAdv: removed unlock time info
- TxConfAdv: added fiat amount display
- TxConfAdv: tx description can now be edited
- Contacts: added a clickable ‘new contact’ icon to the contacts widget
- Receive: added a dialog to create (non-persistent) payment requests
- Coins: fixed an issue that could cause freeze and thaw to fail on multi-account wallets
- Coins: setting a label should no longer sometimes label the wrong coin when wallet contains multiple accounts
- Calc: now accepts pasting full precision amounts
- Mining: redesigned Settings tab to be more streamlined
- Mining: all settings are now saved to config
- Mining: XMRig can now be started with elevated privileges on Linux
- About: UI improvements
- Menu: added a ‘documentation’ action, ‘report bug’ now redirects to a relevant entry in the official documentation
- TxProof: no longer allow creating InProofs for change/churn outputs created in outgoing transactions
- TxProof: removed a misleading error message that showed when trying to create an OutProof when no secret tx key is present
- TxProofVerify: Verifying a tx proof will no longer hang the UI
- macOS: the built-in updater should work again
- macOS: fixed status bar button clickability
- Rebased Monero to latest release-v0.17
Beta-9 changelog (2021-09-19)
- Rebased Monero to v0.17.2.3 (fixes decoy selection bug)
- Tx import: don’t allow duplicate imports
- Support all seed languages for 25 word seeds
- Allow using enters in seed entry
- OpenSSL updated to 1.1.1l
- Removed misc dead nodes
- Transaction proof dialog should now work properly when started from the context menu
- Allow using “.portable.txt” for enabling portable mode
- Add Melo.Tools and blockchair block explorers
- No longer allow manually storing the wallet cache during synchronization
- Misc UI fixes
Beta-8 changelog (2021-06-11)
Features & Improvements:
- Trezor hardware wallet support
- Webcam QrCode scanner
- Note: the scanner is not currently supported on Linux standalone binaries. Download the AppImage if you are on Linux and want to use this feature.
- You can now paste a QrCode image directly into the Pay To field and it will automatically fill in the address (and description, amount if it is a payment request):
- QrDialog: QrCode now scales with the size of the dialog.
- Multi-input sweeps: You can now select multiple coins in the Coins to sweep in a single transaction.
- Coins can now be labeled.
- Note: labels are currently tied to the transaction description. Let me know if your use-case requires finer control.
- A search bar was added to the Coins tab.
- Unconfirmed transactions are now stored in the wallet cache and can be rebroadcast after the is re-opened. Prior to this update rebroadcasting was only possible as long as the wallet remained open after sending a transaction.
- During initial setup the presence of local node on the default port is detected. Feather will automatically suggest connecting to it instead of a third party node.
- Added a tool to check if an address: 1) is valid, 2) belongs to the currently opened wallet, 3) which subaddress account it belongs to. You can access it by going to Tools -> Address checker.
- The list of mining pools in the Mining tab can now be configured.
- Updated built-in Tor to v0.4.6.6 (Windows / Linux)
- Linux release builds should now be permanently reproducible
- A button to show transaction details was added to the dialog that appears after successfully sending a transaction.
- Password entry is now required to open the seed, keys dialog.
- Dummy outputs are now labeled in the advanced transaction confirmation dialog.
- Added an “Open link” button on various message boxes that include a link
- Updated the hardcoded node list: added more high performance nodes and removed dead nodes and v2 hidden services
- Contacts: switch name and address column
- The list of recently opened wallets can now be cleared.
- Reduced AppImage size by 22% (31 -> 24 MB)
- Reduced standalone Linux binary size by 35% (76 -> 49 MB)
Fixes:
- Fixed an issue that could cause the wizard to stay open after opening a wallet
- –stagenet and –testnet command line flags work again
- Closing a wallet will no longer cause the wizard to hang temporarily
- Fixed an issue that could cause a wallet to fail to open if the wallet cache was missing
- Minor UI fixes
Beta-7 changelog (2021-05-27)
Features:
- Multiple wallets can now be opened at once (File -> Open wallet)
- Added support for subaddress accounts (Wallet -> Account)
- Tray icons are now enabled on Windows and macOS
- A list of recently opened wallets was added to the File menu
- Fiat and cryptocurrencies shown in the Calc tab are now configurable
- Choose between 200+ fiat currencies and 100+ cryptocurrencies.
- Balance display in status bar is now configurable in settings
- The seach bar on the History, Send and Receive tabs can now be toggled with Ctrl+F
- A threshold for clearnet synchronization can now be set for the “All traffic over Tor, except initial wallet sync” option in Tor settings
Bugfixes:
- Fixed an issue that could cause newly created wallets to sync from genesis
- Fixed an issue that could cause the 25 word seed to be missing from the seed dialog
- Fixed an issue that could affect the reproducibility of AppImage builds
- Manual transaction import and broadcasting should now work when connected to a local node
- The definition of a local node was expanded to include nodes on local networks
- Balance shown in the statusbar is now affected by the amount precision setting
- Sorting the History tab by date should now properly sort the items
- LocalMonero: disable search button during search
- The amount field in the Send tab is no longer cleared when the Pay to field is edited
Misc:
- Added wallet creation date to debug info
- The title now shows the active subaddress account index
- Use white icons on the Calc and LocalMonero tab if dark mode is active
- Added a button to copy the address in the Transaction Proof dialog
- Hovering over the Qr code on the Receive tab now shows a pointer cursor to indicate that it is clickable
- Added a link with instructions on how to setup udev rules for Ledger users on Linux
- Fixed an issue that could cause buttons to squish in dark mode
- Fixed a compilation issue with GCC 11
- Fixed various compiler warnings
Beta-6 changelog (2021-05-05)
Ledger support:
- The long awaited Ledger support is finally here!
- Ledger wallet synchronization is 6-7x faster than the GUI
- Wallet creation and subaddresses generation are instantaneous
- The view key is stored in the encrypted wallet file, therefore will only have to export your view key once during wallet creation
- If the device is disconnected during operation, the wallet will show a dialog and ask if you want to try to reconnect
- If an error occurs, a descriptive message is shown on how to resolve the issue
- Trezor support will be added in a future update
Updater:
- A message is shown in the statusbar when a new Feather update is available
- The download is verified against a hash signed with the release signing key
- The update will be extracted and stored in the same directory as the current binary
LocalMonero:
- Search for LocalMonero listings based on amount / currency / location / payment method
- Double-click on a listing to view offer details.
Tor networking improvements:
- The Tor info dialog was redesigned
- You can now set the host and port of the local Tor daemon
- Select between three different modes:
“Route all traffic over Tor, except traffic to node”
All traffic to the Monero Daemon RPC is routed over clearnet. This option is automatically enabled when Feather is connected to a local node.
“Route all traffic over Tor, except initial wallet synchronization”
This is the default. The wallet will sync over clearnet and automatically switch to a .torify.net node after this is finished. Synchronization requires a lot of data transfer is therefore very slow over Tor.
“Route all traffic over Tor”
This option is automatically enabled on Tails and Whonix or when Feather is started using Torsocks.
- When Feather is started for the first time, you will have the chance to configure the Tor settings and node before any network connections are made
Misc:
- Lots of refactoring
- Monero updated to v0.17.2.0
- Balance displayed in the status bar is no longer rounded
- Fixed an issue that could cause the History tab to be incomplete after wallet sync
- Fixed an issue that could cause Feather to crash after opening a wallet
- Libwallet: The client secret is reset upon connecting to a different node
- Libwallet: fixed an issue that could cause Feather to get stuck while creating a transaction
Beta-5 changelog (2021-03-24)
Notice:
- Windows users: The default config directory was changed to
%appdata%/FeatherWallet. If you wish to retain your old config, move the contents of%userprofile%\.config\featherto the new location.
History page:
- Columns can now be hidden and reordered
- Right click the table header for options
- History layout is persisted in the config
- A txid column was added (hidden by default)
- Amount sort should now work as expected
- Tx description of pending transactions can now be changed
- Amount precision as displayed in the amount column can be changed in settings
- The fiat column once again shows the historical fiat price (instead of “?")
- Description can now be copied from the context menu
- Pressing Ctrl+C with a tx selected will now copy its txid to the clipboard
- Date and time format can now be configured in the settings
Transaction proofs:
- A new dialog to create transaction proofs was added
- To access it right click on a transaction -> “Create tx proof” or via the transaction information dialog.
- Proofs can now be output in a new PGP-like message format.
- It contains all the necessary information to verify the proof signature, including an optional message.
- Formatted proofs can be verified easily in the “Tools -> Verify transaction proof” dialog.
- Descriptive messages will be shown when generating a particular tx proof is not possible due to missing tx key, or other issue.
Transaction info:
- Information shown in the tx info dialog is now more descriptive
- The old transaction proof creation widget was removed
- Multiple tx info dialogs can now be open at the same time
Receive page:
- Subaddresses can now be hidden
- Checkboxes were added to show used / hidden subaddresses
Send page:
- The “Pay to” field on the send tab should no longer have clipping issues
- Pressing tab on the “Pay to” field will now move the cursor to the next field instead of inserting a tab character
Sweep output dialog:
- When splitting an output a estimated output calculation is shown. e.g. “1 XMR ≈ 5x 0.2 XMR”
Networking:
- The network status is more responsive
- The dreaded “? blocks remaining” message should be gone for good
- Closing the wallet during synchronization will now immediately close the wallet (Network reads are cancelled on wallet close)
- Fixed an issue that could cause the wallet to erratically switch between nodes (common on Whonix)
- Refreshing is paused during transaction construction
- Transaction construction now requires an order of magnitude less bandwidth (The output distribution is cached and supplemented when needed)
Multibroadcasting:
- To further mitigate the “double spend” issue that is caused by poor transaction propagation, outgoing transactions are now broadcast to all available websocket nodes over Tor by default, in addition to the current node.
- This feature can be disabled in the settings
Wizard:
- The UI flow was improved
- It is now possible to specify a seed offset passphrase when restoring a seed
- A dark mode toggle was added to the menu
- Fixed an issue that could trigger a crash after pressing the Generate button on the create seed page
- Now automatically suggests a wallet name that hasn’t been used when creating a new wallet
- Setting a password now requires entering it twice
Portable mode:
- To enable portable mode create a file named “.portable” in the same directory as the executable
- All configuration and wallet files will be saved relative to the executable in “./feather_data” by default
Torsocks:
- Fixed an issue that prevented Feather from loading Reddit/CCS/Fiat prices, etc.
- When Feather is started with Torsocks .torify.net nodes will be used
Misc:
- Tor was updated to 0.4.5.7
- Restore height for newly created wallets is set to latest blockheight (if available)
- Trying to open the seed dialog on view-only or non-deterministic wallets will now show a message that a seed is not available
- Fixed an issue that could cause debug info dialog to block UI
Beta-4 changelog (2021-02-06)
Features:
- Multi-destination transactions
- Windows release binaries are now reproducible
- AppImages are now reproducible
- Seed: enable erasures (replace a word with “xxxx” and recover the full seed)
- XMR.to exchange integration was removed
Wallet:
- RandomX is no longer linked (should help mitigate against AV false positives)
- Speedup wallet restores by skipping unneeded blocks in fast refresh
- Include unconfirmed payments in balance calculation
UI:
- Color scheme was improved
- The Home tab is now hideable
- Statusbar: Balance is displayed more concicely
- Wizard: sort wallets by last modified
- Wizard: seed display was improved
- Wizard: allow double clicking to open wallet
- Wizard: add button to copy seed to clipboard
- History: a notice is shown when the wallet is still synchronizing
- Settings: You can now select the Reddit frontend to use when opening a link
- Reddit: Right click -> Copy link
- Whonix: whonix version is detected and shown in the debug dialog
- TxConf: show message when churn transaction detected
- TxInfo: UI was improved
- History: allow filtering by subaddress label
Bugfixes:
- Send: don’t lose precision on amounts
- Clear all tables when wallet is closed
- Nodes: fallback to hardcoded list if no nodes were previously cached
- Nodes: don’t show the exhaustion warning in some scenarios
- Coins: fix an issue that could cause freeze/thaw to select the wrong index
- Fix a crash that could occur when the wizard is closed after trying to open a wallet
- Update balance immediately after sending a transaction
- Always store wallet on exit
- Update the Tor binary on filesystem if embedded version is higher
Misc:
- Monero updated to v0.17.1.9
- Tor updated to 0.4.5.5-rc
- Wallet cache debug dialog added
- Various build system improvements
- Reduced Windows binary size by 60%
Beta-3 changelog (2020-12-25)
Features:
- MorphToken integration was removed (they now block all Tor traffic).
Wallet:
- Wallet is now saved immediately upon finishing wallet refresh
- Feather will no longer sometimes display subaddresses belonging to non-primary accounts for wallets that were created with the GUI
- Websocket connection is now kept alive
UI:
- Wizard: Open wallet page was redesigned
- Wizard: New banner design
- Wizard: “Open wallet” is now autoselected if any wallets are detected
- Status: Wallet refresh shows blocks remaining instead of absolute values
- Status will now show an animated message during transaction construction
- Home: Text in table widgets is now word wrapped
- DebugInfo: Websocket status message is more concise
- DebugInfo: A new entry was added that shows if the wallet only contains funds in the primary account
- History: Formatting of fiat amounts is now locale-aware
- History: It’s no longer possible to rebroadcast incoming transactions
- TxInfo: Tx proofs now have clickable help labels with information about what each proof proves
- Contacts: It’s no longer possible to add duplicate addresses or labels
- Send: “Pay to”, “Description” and “Amount” are now clickable help labels
- Amounts are now justified in the transaction confirmation dialog
- External link warning no longer warns about not using Tor on Tails/Whonix
- Non-breaking spaces were removed from currency strings
- Fully funded CCS proposals are no longer hidden
- Fixed a bug that could cause the send button to remain disabled after a new wallet is opened
- Attempting to send a transaction when the wallet is not connected to a daemon will now show an error
- Nodes: double click on a node to connect
- Clicking the balance label will now pop up a dialog with a more detailed balance overview
- The default wallet directory can now be changed
Misc:
- Minor build speedup
Beta-2 changelog (2020-12-05)
Features:
- Failed transactions can now be rebroadcast (as long as the wallet remains open)
- Rescan spent was added to Wallet -> Advanced
Wallet:
- Wallet is now saved immediately after sending a transaction (instead of waiting up to 60 seconds)
UI:
- Home widgets can now be switched between using tabs
- Exchange integrations have been consolidated to a new “Exchange” tab
- XMRig settings UI was squished to take up less vertical space
- XMRig tab was renamed to “Mining”
- Icon for the Calc tab was changed
- Seed dialog UI was improved
- Coins: labels can now be copied from the context menu
- Percentage label is no longer displayed on balance ticker
- Message boxes now have a single button when no choice has to be made
- MorphToken: some missing trade states are now accounted for
- TransactionInfoDialog: Blockheight no longer shows zero for unconfirmed transactions
- Fiat conversion label now updates when the Send page is autofilled
- Improved Tor status on Tails in Debug info dialog
- Menu: disabled “Open wallet” action was removed
Security:
- OpenSSL updated to 1.1.1i (CVE-2020-1971)
Misc:
- Monero updated to v0.17.1.7
- Feather no longer comes bundled with a XMRig binary
 is a phishing site, beware!
is a phishing site, beware! Onion
Onion I2P
I2P